Security Information
Last updated: October 30, 2013
The test set can perform security procedures during the following call processing operations:
- Location Update (Registration) Procedure
- Radio Bearer Test Mode Origination to CELL_DCH - CS Domain (Non-HSPA or HSDPA)
- Test Set Initiated AMR Voice Service Start
- UE Initiated AMR Voice Service Start
- UE-Initiated UE-to-UE Video Call Origination Ladder Diagram (lab application or feature-licensed test application only )
- GPRS Attach (lab application only )
- Test Set Initiated GPRS Detach (lab application only )
- UE Initiated GPRS Detach (lab application only )
- Test Set Initiated GPRS Service (lab application only )
- UE Initiated GPRS Service (lab application only )
- UE Initiated GPRS Service, Activate PDP Context Reject (lab application only )
- UE Initiated CS Data Service Start Procedure (lab application only )
You can specify which security procedures are performed during these operations (None , Auth & Int , or Auth Only ) using the Security Operations setting. Authentication and integrity protection are described in 3GPP TS 35.206, 24.008, 33.102, 25.331, and 35.202.
During authentication, both the UE and the network confirm that the other is valid by a series of computations based on a shared secret Authentication Key (K). The computations are performed using one of two Authentication Algorithm s, with K, SQN and the signalled values for Random (RAND) Value and AMF Value as inputs.
When integrity protection is enabled, the network encodes every RRC message with a digital signal (IK, which is derived from K, SQN, RAND and AMF). The UE rejects all RRC messages (except TC messages) that do not bear the proper digital signal.
Security Parameters
- Security Operations
Security Operationscan be set to:None: No security procedures are performed during call processing operations.-
Auth & Int: Both authentication and integrity protection are performed during call processing operations. -
Auth Only: Only authentication is performed during call processing operations. -
Auth, Int, & Ciph:Authentication, Integrity Protection and Ciphering is performed during call processing operations.
GPIB command: CALL:SECurity:OPERation
- Authentication Algorithm
The test set supports both the normal operation authentication algorithm (
Milenage (Rijndael)) and the conformance test algorithm described in 3GPP TS 34.108 (Test 34.108).GPIB command: CALL:SECurity:AUTHenticate:ALGorithm
- Authentication Key
32 hex digits representing the 128-bit subscriber key (K). The default value of
Authentication Keymatches the Keysight USIM's "Applicative Key" as described at www.keysight.com/find/usim.GPIB command: CALL:SECurity:AUTHenticate[:KEY]
- Operator Variant Parm Type
This setting specifies whether the Operator Variant Auth Alg contains the OP or OPc. If
Operator Variant Auth Algcontains OP, the test set calculates OPc as per 3GPP TS 35.206.GPIB command: CALL:SECurity:AUTHenticate:OPVariant:PTYPe
- Operator Variant Auth Alg
32 hex digits representing either the 128-bit OP or OPc. You must indicate, using the Operator Variant Parm Type setting, whether this setting contains OP or OPc.
GPIB command: CALL:SECurity:AUTHenticate:OPVariant:PVALue
- Random (RAND) Value
32 hex digits representing the 128-bit random challenge.
GPIB command: CALL:SECurity:AUTHenticate:RANDom
- AMF Value
4 hex digits representing the 16-bit authentication management field.
GPIB command: CALL:SECurity:AUTHenticate:AMF
- IMEISV Request State
Specifies whether UE is requested to report its IMEISV (The International Mobile station Equipment Identity and Software Version Number) value via Authentication and Ciphering Response message.
The IMEISV is composed of the following elements:
- Type Allocation Code (TAC). Its length is 8 digits.
- Serial Number (SNR) is an individual serial number uniquely identifying each equipment within each TAC. Its length is 6 digits.
- Software Version Number (SVN) identifies the software version number of the mobile equipment. Its length is 2 digits.
GPIB command: CALL:SECurity:EISV:REQuest[:STATe]
Reset Authentication SQN
The authentication sequence number (SQN) is set to zero each time the test set is powered on. It then increments each time an authentication procedure is performed. The SQN can be reset to zero by selecting Reset Authen. SQN or sending the CALL:SECurity:AUTHenticate:SQN:RESet[:IMMediate] command.
Security Results
During the authentication procedure (see Security Ladder Diagrams ), the test set sends an Authentication Request message to the UE which contains RAND and AUTN (which is derived by the test set from K, SQN, AMF and RAND). If the UE determines that the AUTN contains a valid SQN and MAC, it sends an Authentication Response message to the test set, which includes RES. If the test set determines that the RES is valid, it returns an Authentication Result: MM or Authentication Result: GMM result (depending upon which domain has been authenticated) of Success . Otherwise, the test set sends the UE an Authentication Reject message and returns an Authentication Result of Incorrect RES Length or RES Does Not Match .
If the AUTN sent by the test set to the UE contains an invalid MAC or SQN, the UE sends an Authentication Failure message with the appropriate Cause information element (and AUTS if the failure cause is Synch Failure ; the test set then initiates the re-synchronization procedure). The test set then reports this Cause value in both the Authentication Result (MM or GMM) and in the UE Reported Failure Cause result. For example, you can induce a MAC Does Not Match authentication failure as shown below by changing the Authentication Key setting in the test set to NOT match that in the UE's USIM (note that when using the Test 34.108 Authentication Algorithm , the mismatch must occur in the first 8 hex digits in order for authentication to fail).
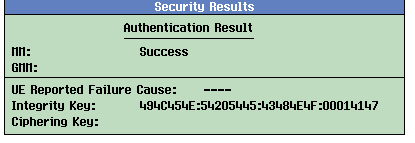
Authentication Result
The authentication results reported by the test set include:
- Success
- MAC Does Not Match: if UE Reported Failure Cause = 20.
- Synch Failure: if UE Reported Failure Cause = 21.
- Unknown: if UE Reported Failure Cause is any value other than 20 or 21.
- Incorrect RES Length: if the RES Length is other than 8 bytes.
- RES Does Not Match
Authentication results are reported separately for the packet switched (PS) and circuit switched (CS) domains:
- Authentication Result: MM
This result indicates the success or failure of the UE and test set to authenticate in the CS domain.
GPIB command: CALL:SECurity:AUTHenticate:RESult[:MM]?
- Authentication Result: GMM
This result indicates the success or failure of the UE and test set to authenticate in the PS domain.
GPIB command: CALL:SECurity:AUTHenticate:RESult:GMM?
UE Reported Failure Cause
The UE Reported Failure Cause can be any number between 1 and 255. 3GPP TS 24.008 s10.5.3.6 and s10. 5.5.14 provide mappings of the numeric values to their equivalent causes. The causes relevant to authentication are shown below (see 3GPP TS 24.008 s4.3.2.5.1 and sG.3).
GPIB command: CALL:MS:REPorted:AUTHenticate:FAILcause?
Integrity Key
If the Security Operations is set to Auth & Int or Auth, Int, & Ciph for the security procedure, the test set reports the Integrity Key being used. This results can also be queried by CALL:SECurity:RESult:INTegrity:KEY? .
Ciphering Key
If the Security Operations is set to Auth, Int, & Ciph for the security procedure, the test set reports the Ciphering Key being used. This results can also be queried by CALL:SECurity:RESult:CIPHering:KEY? .
|
|